-
Audit
Auditing increases the reliability of your company information for decision-makers and users – it’s a matter of credibility and trust.
-
Assurance
We have established Assurance Service Lines in the area of audit-related consulting so that we can support you in identifying the risks and challenges relevant to you.
-
Technology consulting
Receive customised technology consulting
-
Operational excellence and restructuring
Advisory for businesses, whatever situation they’re in
-
Deal Advisory
We’ll advise you on national and international transactions
-
Valuation & economic and dispute advisory
We’ll value your business fairly and realistically
-
Tax for businesses
Because your business – national or international – deserves better tax advice.
-
Private Clients
Wealth needs trust, transparency and clever minds. We can do that!
-
Business Process Solutions
Measuring and utilising company data
-
Real estate tax
Real estate taxation – we provide answers to your questions!
-
Tax for financial institutions
Financial services tax – for banks, asset managers and insurance companies
-
Tax in the public sector
Advisory and services for the public sector and non-profit organisations
-
Employment law
Representation for businesses
-
Commercial & distribution
Making purchasing and distribution legally water-tight.
-
Compliance & directors’ liability
Avoiding liability at your company
-
Inheritance and succession
Don’t leave the future to chance.
-
Financial Services | Legal
Your Growth, Our Commitment.
-
Business legal
Doing business successfully by optimally structuring companies
-
Real estate law
We cover everything on the real estate sector.
-
IT, IP and data protection
IT security and digital innovations
-
Litigation
Designing solutions – we’re your partner for successfully resolving disputes
-
Mergers & acquisitions (M&A)
Your one-stop service provider focusing on M&A transactions
-
Restructuring & insolvency
Securing the future in the crisis.
-
Energy, telecommunications and public economic law
Comprehensive advice in energy law, telecommunications law, public commercial law & regulated markets.
-
Technology consulting
IT enables business
-
IT assurance
Rapid technological change is a sign of our times.
-
Tax Technology
Digitalisation for tax and finance departments
-
IT, IP and data protection
IT security and digital innovations
-
Public sector
Digitalisation, processes & projects
-
Cyber Security
Advice and services for the mid-market in Germany
-
Security consulting
Stay on course, even in stormy times
-
Sustainability strategy
Laying the cornerstone for sustainability.
-
Sustainability management
Managing the change to sustainability.
-
Legal aspects of sustainability
Legal aspects of sustainability
-
Sustainability reporting
Communicating sustainability performance and ensuring compliance.
-
Sustainable finance
Integrating sustainability into investment decisions.
-
International business
Our country expertise
-
Entering the German market
Your reliable partners.
-
Consulting for Stadtwerke and municipalities
Expertise for a sustainable future
-
Security consulting
Stay on course, even in stormy times
-
Public sector
Digitalisation, processes & projects
Why mid-market companies should now be thinking about cybersecurity:
- Cybersecurity is a matter for all kinds of businesses, but especially for those in the mid-market. Data protection and the protection of critical infrastructure (KRITIS) are central topics for the future – including for mid-market companies.
- IT and digitalisation are penetrating all areas of mid-market companies. This makes protecting data and systems one of management’s central responsibilities – including at mid-market organisations.
- The Federal Office for Information Security (BSI) and the IT Security Acts (Umbrella Law and Version 2.0) provide the framework for successful and legally watertight cybersecurity.
Grant Thornton is an authorised partner (advanced persistent threat responder) of the Federal Office for Information Security (BSI) for cyber-attacks.
![]()
“We’ll help you protect your organisation and your organisation’s assets. When it comes to cybersecurity, our experienced teams can always help.”
Thomas Takkin, Partner at Grant Thornton Germany
Cybersecurity 2024
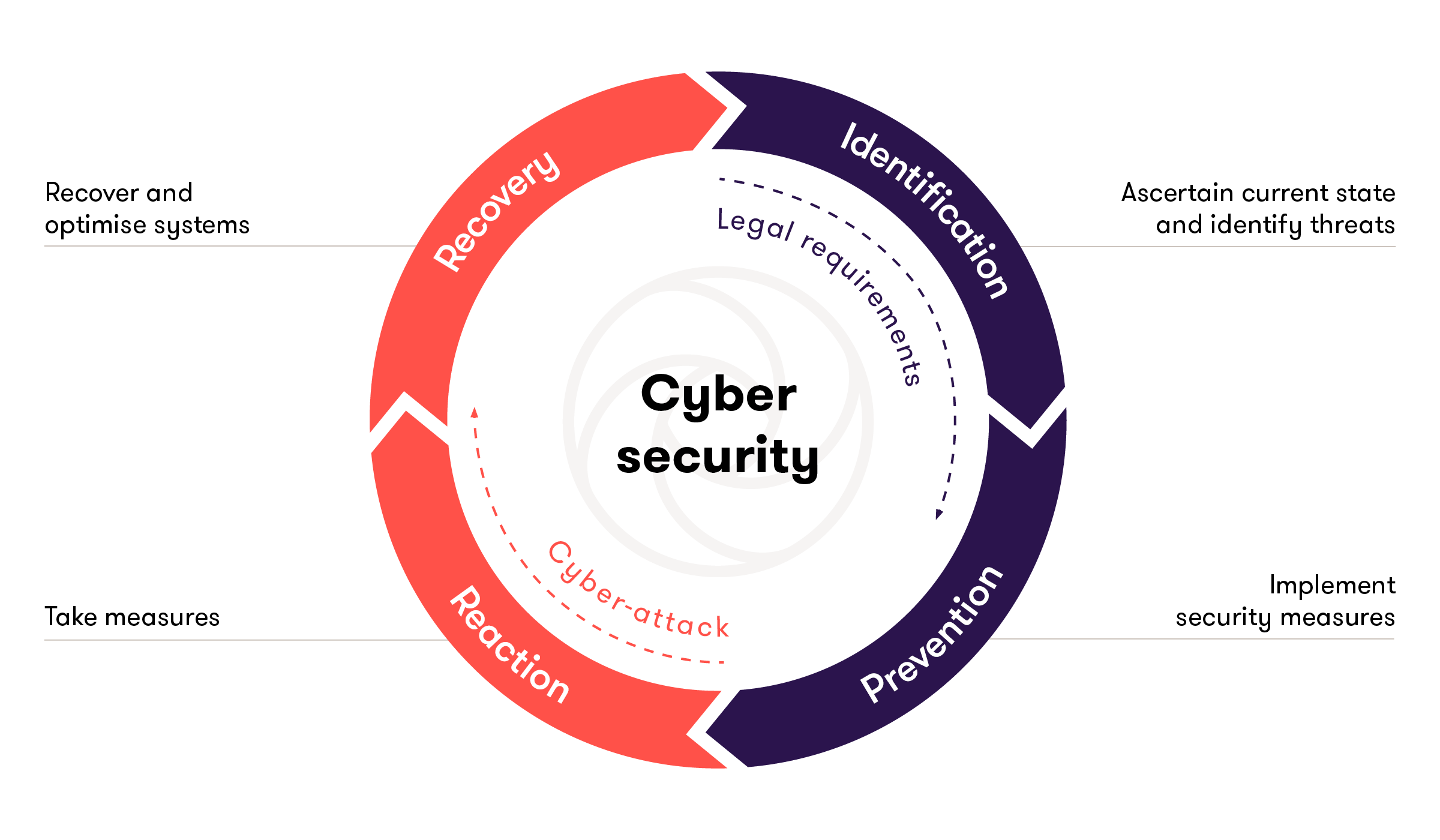
We are there to help with:
- Implementing legal requirements
- Analysing your existing IT infrastructure
- Safeguarding the value of your organisation against digital attacks
- Emergencies
- Reanimation and continuous assistance with the learning process with respect to cybersecurity
We generate a current status analysis and deliver a risk assessment using the following tools:
- Cybersecurity health check: standardised approach to evaluating security measures. This check is based on ISO/IEC standard 27001.
- IT risk assessment: an IT security risk assessment in which we scrutinise your organisation’s assets, data and information systems, and analyse the potential effects that threats to your systems could have.
- Basic legal assessment: an analysis of potential legal consequences and litigation risk to your organisation.
We’ll implement specific security measures as preventive protection for your organisation using the following methods:
- Cyber-defence centre: we monitor your IT 24/7 as required!
Penetration and vulnerability tests: We’ll test your cybersecurity resilience regularly and specifically. - Information security management systems/ISMS: we’ll define and carry out regular checks on your policies, procedures and responsibilities to safeguard information security within your organisation.
- NIST cybersecurity framework 2.0: a comprehensive approach that results in improving risk management and increasing cybersecurity.
- The Digital Operational Resilience Act (DORA): implementation of your organisation’s duties under DORA on the harmonisation of cybersecurity in the financial sector across Europe.
In the event of a cyber-attack, we’ll help you take the right steps without delay. In this way we safeguard your organisation’s assets, help you fulfil your reporting obligations and keep you continually able to operate with the following measures:
- Cyber-incident response – with us, take all the right steps in the event of a cyber-attack!
- Digital forensic investigations: we’ll help you to prove the theft of data that can be used in evidence.
- E-discovery and managed document review: we’ll use electronic investigation methods for you as a basis for evidence that can be used in court
- Consulting on data protection law
Avoid shutdowns and stoppages from a cyber-attack and evaluate them! We’ll help you to recover your systems as quickly as possible and work with you to constantly improve your systems.
- Disaster recovery: analysis of the cyber-attack.
- Crisis management: check of existing processes, and improvement as necessary.
- IT expert opinions: As the basis for potential liability claims.
- IT, IP and data protection consulting.
Almost 80% of all organisations have registered one or more cyber-attacks within the last twelve months.![]()
Only 23% can attest to not having registered a cyber-attack on their IT within the past year. For 18%, an attack on their IT occurs at least once a month.
About one in four organisations do not analyse any data on cyber-attacks – an indication of a false sense of security.
(Source: Grant Thornton study)
What is cybersecurity?
Cybersecurity comprises technologies, practices and measures that can protect an organisation’s IT. Information and data are the main capital of mid-market companies. So by using cybersecurity measures they are protecting their assets. These include traditional favourites like firewalls and anti-virus programs, but also regular training courses for staff on how to use IT and data. A clear contingency plan is also needed for emergencies. In the event of a cyber-attack, who should do what and when? Who is to be informed and how?
The Umbrella Law and the amendments in version 2.0 of the IT Security Act provide the guidelines and legal basis for cybersecurity. Critical infrastructures, abbreviated to KRITIS, are a particular focus here. Critical infrastructure is defined as infrastructure that is of critical importance to society. If these organisations fail, this will have an effect on public order, safety and security. Which sectors and organisations are on the KRITIS list depends on how critical they are to public life.
IT security and cybersecurity – effectively dealing with cyber-risks at mid-market companies
Cybersecurity is becoming ever more important. Experts today are no longer asking if companies are going to be the victims of an attack – the only question is when. This needs to be prevented and the necessary measures taken. The Federal Office for Information Security (BSI) has marked out the conditions with the IT Security Act. But even in the event of an attack, it’s not too late. The Grant Thornton experts are at your side at all times – both for prevention and in an emergency.
FAQ cyber security
Cybersecurity is vital to safeguard company information from unauthorised access by third parties. Personal and business data are valuable. Cybersecurity measures ensure that valuable data are not lost or stolen through cyber-attacks. Cybersecurity pays off in the following aspects of company security:
- Identity protection,
- Protection from financial loss
- Protection from reputational damage
- Preservation of privacy – both of the clients and staff of your organisation
- Safeguarding of information that is critical to business
- Compliance with legal provisions and, last but not least
- Protection from cyber-attacks
Companies today are under massive pressure regarding cybersecurity, and the size of the organisation is playing less and less of a role – it can affect anyone. Data and the organisation’s reputation are valuable. Making sure this is safe is a job for management which has a high priority.
The overall cost of cybersecurity cannot be estimated. It depends on the size of the organisation and the number of staff. The business model, sector and current digital status also play a role.
The costs are affected by the scope of the security measures to be taken, internal and external personnel expenses, technology costs for software and hardware solution, legally prescribed compliance requirements on the industry (also see KRITIS requirements), the organisation’s risk management system, training and awareness of staff and steps necessary to identify incidents.
Experience shows, however, that the costs for prevention and setting up cybersecurity are always smaller than the costs that an attack can create.
We recommend undertaking to record the current status by means of a comprehensive survey and a risk assessment. This will allow you to identify vulnerabilities in your digital infrastructure. Focus on your most critical assets and data and implement clear security guidelines. Train your staff regularly. A disaster recovery plan should also be prioritised in order to be able to deal with a cyber-attack quickly. Cybersecurity insurance can also offer additional protection. We will be glad to assess the conditions and effectiveness of this kind of insurance for your organisation.
To be able to give an accurate recommendation, we first have to establish which systems are in use. This requires undertaking a comprehensive survey of the IT infrastructure, followed by a risk assessment and action. KRITIS guidelines also need to be complied with and questions answered, such as: is your organisation a provider of critical infrastructure? Do you have a duty to report or be certified? We recommend drafting a contingency plan that defines contact persons and includes simulated emergency training (penetration tests, vulnerability scans).
Legislation like the General Data Protection Regulation (GDPR) and the liability of directors are relevant to companies and management. Sector-specific regulatory requirements such as ISO/IEC 27001, KRITIS, MaRisk, VAG, TISAX, the BSI Act also have to be complied with.
A cybersecurity consultant is an expert in the development, implementation and maintenance of effective cybersecurity measures at an organisation. His or her job is to protect information systems, networks and data from threats in the virtual realm.
In selecting cybersecurity consultants, you should make sure that they are up-to-date with the latest technical developments. The internet changes fast and hackers across the globe are creative – and so cybersecurity experts have to be too in order to work effectively.
The phrases cybersecurity and IT security are often used interchangeably. But there small differences between the two terms. IT security includes physical measures that prevent the loss of data. This also involves access controls and security guidelines – online and offline. Cybersecurity primarily concerns itself with attacks from outside by hackers or malware.
Both IT security and cybersecurity need to have their place and have to be kept up-to-date.
Today, cybersecurity is a crucial part of business security. It is a part of things today just as much the alarm system on the company premises and is the result of increasing digitalisation. It serves to:
- Protect from financial loss
- Safeguard information that is critical to business (including intellectual property)
- Preserve the company’s reputation
- Comply with legal provisions
- Prevent interruptions to operations
- Protect against data and identity theft, and
- Prevent breaches of data protection.
Digital networking makes it necessary for organisations to also protect and secure themselves in the virtual realm. Cyber-attacks are a part of everyday life today and no longer only affect large multinationals, but organisations of every size. Customer data, intellectual property, and even the organisation’s reputation are at risk.
Cybersecurity today is part of every organisation’s basic security measures. It provides protection from cyber-attacks, financial and data loss, ensures the continuity of business and the security of personal data. It preserves the organisation’s reputation and compliance with legal provisions. Cybersecurity is particularly crucial for organisations included under critical infrastructure (KRITIS). With these, there is a public interest in cybersecurity and the requirements on them are particularly strict.
Emergency number for cyber-attacks
We provide assistance 24 hours a day in the event of cyber-attacks. You can reach us at:
0800 1701000
Take advantage of tailor-made updates with our free newsletters and webinars. Bring your business on for the long-term.
Our awards
We’re proud of the awards we’ve won. And we’re just as happy that our clients give us top ratings! We’re working hard to keep it that way. And that’s a promise!
 |
 |
 |
 |





